Introduction
Traditional network architecture was built with the concept of a perimeter network where once someone was on the network, there was an implicit level of trust. The shift toward cloud hosting, remote work and other modernization has created challenges with a traditional perimeter network architecture.
These challenges can be addressed by implementing a Zero Trust Architecture, which ensures that all traffic in and out of a business is verified and authorized. Implementing a Zero Trust Architecture can be done in steps without disrupting employee productivity and connectivity.
This guide was built by security experts to provide a vendor agnostic Zero Trust architecture and example implementation timeline. The timeline assumes that an organization is beginning their Zero Trust journey from scratch, but is meant to be useful for all organizations.
There are seven major components to organizational security that need to be considered when it comes to implementing a comprehensive Zero Trust Architecture. Your implementation order does not need to match how they are listed in the component and reference architecture sections below.
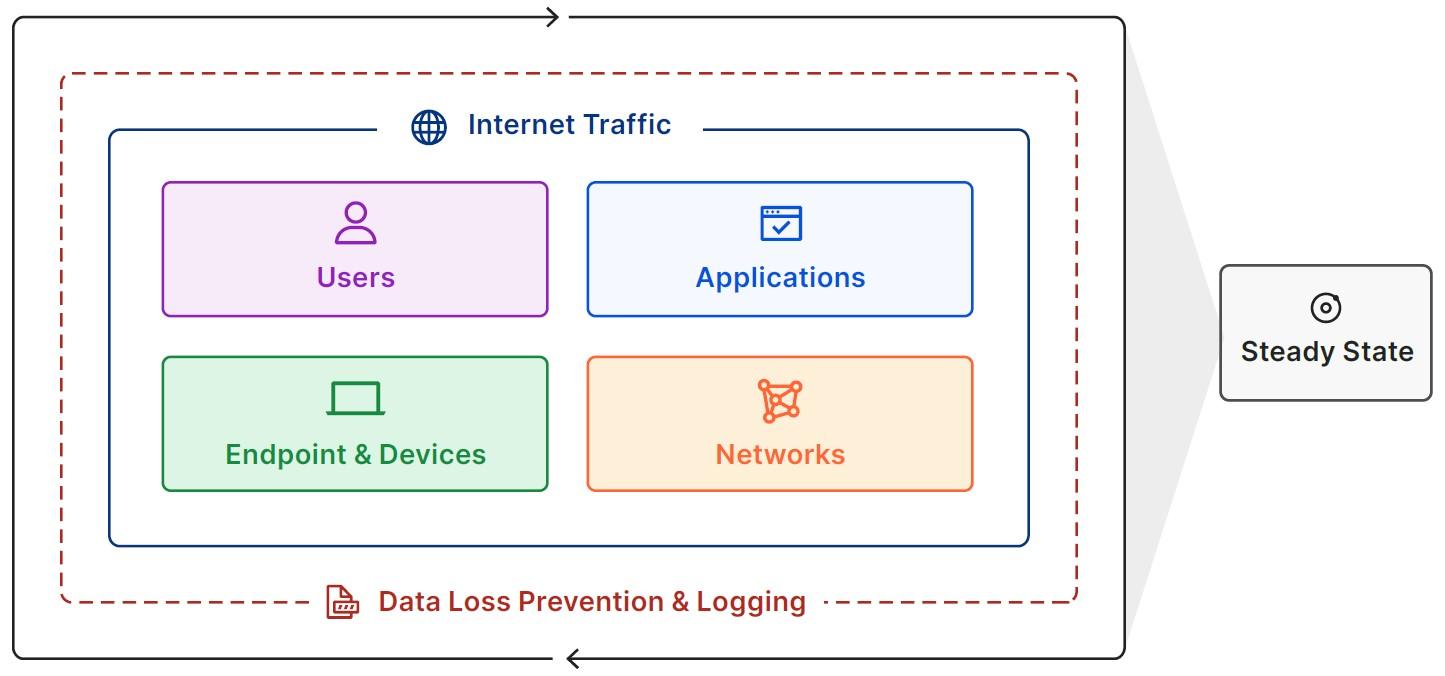
The Roadmap to Zero Trust
Users
Users include employees, contractors and customers. To implement Zero Trust, an organization
must first have an accurate picture of who should actually be trusted, and with what — otherwise
known as Identity. Then it must establish a way to securely authenticate the identity of its users.
Endpoints & Devices
Endpoints and Devices include any device, API or software service within an organization or that have access to organizational data. Organizations must first understand their full set of devices, APIs and services. Then Zero Trust policies can be implemented based on the context of the device, API and service.
Internet Traffic
Internet Traffic includes all user traffic destined for websites outside of an organization’s control.
This can range from business related tasks to personal website usage. All outbound traffic is
susceptible to malware and malicious sites. An organization must establish visibility and control
over user traffic destined for the Internet.
Networks
Networks include all public, private and virtual networks within an organization. Organizations must first understand their existing set of networks and segment them to prevent lateral movement. Then, Zero Trust policies can be created that granularly control which segments of a
network that users, endpoint and devices can access.
Applications
Applications include any resource where organizational data exists or business processes are performed. Organizations must first understand the applications that exist and then establish Zero Trust policies for each application or, in some cases, block unapproved applications.
Data Loss Prevention & Logging
Once you have established all the Zero Trust elements of your architecture to this point, your architecture will be generating large volumes of data on what’s happening inside your network. At this point, it’s time to implement Data Loss Prevention and Logging. These are a set of processes and tools that focus on keeping sensitive data inside of a business and flagging any potential opportunities for data leakage. Organizations must first understand where their sensitive data exists. Then they can establish Zero Trust controls to block sensitive data being accessed and exfiltrated.
Steady State
Once you have built out your Zero Trust architecture for all the other elements of your organization, there are a set of actions you can take to move your organization to a Zero Trust steady state, ensuring consistency with the architecture moving forward.






